All it takes is clicking on a suspicious link to cost yourself or your company tens of thousands of dollars. In this post we will discuss basic concepts related to social engineering attacks.
WHAT IS SOCIAL ENGINEERING?
Social engineering is the exploit of human psychology and susceptibility to manipulation to trick victims into uncovering sensitive information or breach security protocols that allow an attacker access to a network.
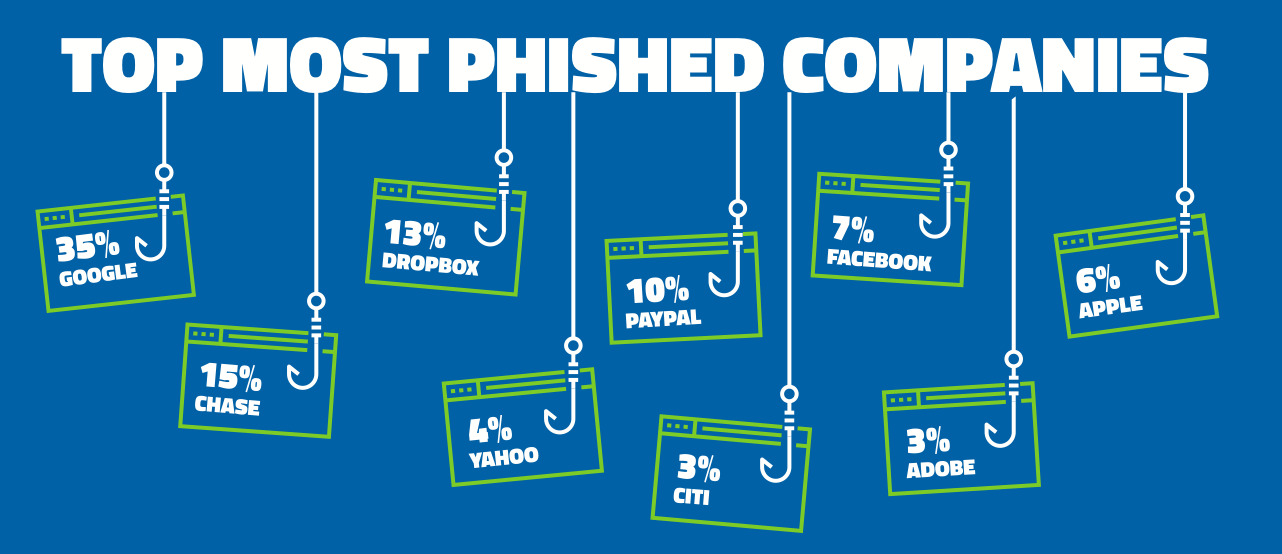
Image-Source: Webroot
EXAMPLES OF SOCIAL ENGINEERING ATTACKS
A technical social engineering attack involves an attacker visiting an organization’s website and retrieves specific emails mostly created with employee’s full names and searching social media accounts that match those. Then checks their profiles if they had listed the target organization as a workplace and sends a friend request to builds up an unsuspecting serious relationship in exchange for information sensitive enough to have access to the organization’s computer/network.
A non-technical form of social engineering involves an attacker dressed up as a fix man/woman who is allowed access into a building. He/she fools the front desk by claiming to be a plumber or electrician on routine maintenance.
Social engineering attacks are quite simple with severe consequences for the organization as they are tough to detect an attacker yet requires no significant skill to carry it out.
TYPES OF SOCIAL ENGINEERING ATTACKS
TECHNICAL
-
Phishing : Attackers create a fake site almost similar to legitimate websites and will trick a user to input private credentials like credit card information and use such to commit fraud.
-
Spear phishing : In contrast to phishing explained above, spear phishing is highly targeted toward either one specific organization, a particular sector within an organization, or an employee.
-
Whaling : Attackers use similar tactics to steal private information only that this time, they phish victims who are bigger fishes as big as whales. I mean the CEO, CFO’s, CTO’s, high ranking public officials, and other top executives. A common type of whaling is Business Email Compromise (BEC), where the sender’s name is the name of a senior executive. Still, the email address is not at the domain of the company, and it is usually unnoticed.
-
Vishing : Like other methods of phishing, the aim is the same, but the medium used is a phone. Attackers use spoofing services to hide their original number and display a different one only to call pretending to be customer service at the target’s bank and demanding private information.
-
Baiting : Attackers offer malicious gifts to unsuspecting victims. Such gifts could be a USB drive already affected with a virus-like trojan to steal information once it is inserted in any computer, or it could be in the form of a free software solution offered for download on the internet.
-
Quid pro quo : An attacker first get hold of damaging information on an individual then offer not to publish the information in exchange for a data compromise in an organization. It’s merely scratch my back I scratch your back or outright blackmail.
-
Pretexting : In a pretexting attack, the attacker poses as a person of trust, such as a family member, someone from the target’s organization, like a member of the IT department or a manager, or any other individual holding authority over the target.
-
Scareware : is often seen in pop-ups telling targets their machine has been infected with viruses and needed to take action immediately to remedy their PC. They can convincingly appear as though they’re coming from a legitimate antivirus software company.
PARTIAL/NON TECHNICAL
-
Impersonation : This is an individual or group pretending to be who they are not. An example is the popular online dating scams.
-
Dumpster Diving : This happens when an attacker searches an organization’s dumpsters and examines electronic or physical storage devices that were not destroyed before disposal to find sensitive information that could be used for exploiting the organization.
-
Shoulder surfing : Here, an attacker looks over the shoulder of a target entering sensitive information like passwords or credit card information to steal.
-
Hoaxes : In a hoax, an attacker creates a prank, fire drill, etc. to cause anxiety so that in the period of panic, he/she gains access to a restricted area or computer not logged out by the authorized user.
-
Tailgating : In large organizations where all co-workers can’t get acquainted, attackers often easily trick employees into yielding access to restricted areas. Usually, by asking that they help open the door because they forgot their access or identity card, or even pleading to help with their computer.
MITIGATIVE MEASURES AGAINST SOCIAL ENGINEERING ATTACKS
-
Develop a personal or your organization’s cybersecurity culture: In an organization where you can afford an IT security expert, he/she would carry out a routine security audit and develop a standard cybersecurity procedure for comprehensive employee’s education. This may include and not limited to proper disposal of electronic and physical information materials, third-party software auditing, regular software updates, avoiding using public networks for sensitive communications, verifying sites SSL security, avoiding unknown links, frequently changing passwords, share only insensitive data via emails, installing software tools protecting against technical social engineering
-
Act like a dummy but think like a detective: Always be skeptical about free offers both online and offline, especially when the circumstances surround your corporate environment.
-
Prioritize your infrastructure: all your networks should be protected from data theft and loss, but infrastructure dedicated to financial transactions and other key information deserves extra security.
-
Keep private information private: open-source intelligence (OSINT) is often used to guess probable security questions and passwords. Do not discuss private business in public. An example of this was when Mcfee accused Binance of having been supposedly hacked; they publicly shared the exchange Bitcoin storage address with thousand of BTC in it to prove it wasn’t hacked. This information as little as it is will lead trace of unmasking illegal crypto spenders back to the exchange as seen here
-
Pentesting: employ qualified external specialists to conduct social engineering attacks to double-check your employees, policies, and physical security infrastructure.
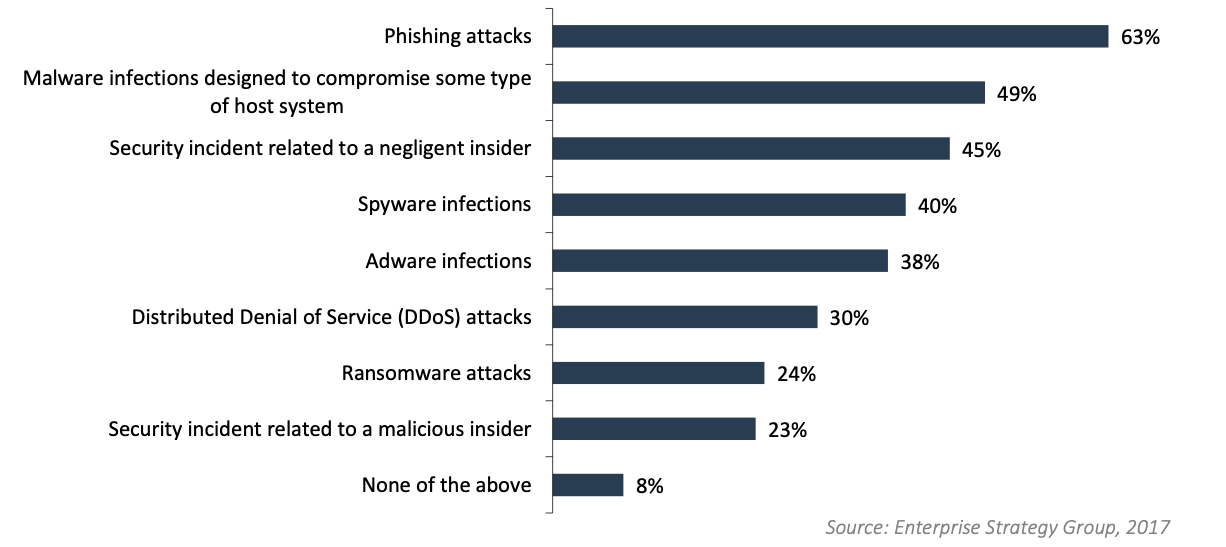
According to Webroot, phishing is the number one cause of breaches for organizations around the world. A recent Webroot sponsored survey of influencers found that 63% have experienced a phishing attack in the last two years, 35% expect to suffer more phishing attacks in the next two years, 43% plan to invest in new threat technology as a result.
One acclaimed solution I am yet to try out is real-time anti-phishing technology.
How does this work?
It uses advanced machine learning and real-time URL validation to spot zero-hour phishing sites in milliseconds, instead of relying on static, outdated lists.
It helps in phishing prevention by keeping your employees away from phishing sites even if they click on malicious links in emails. They are outrightly unable to visit these sites. See phishprotection.com
Another solution is to carry out deliberate attacks on employees to test their security awareness strength and proffer further pieces of training where they fail.
CONCLUSION
Social engineering attacks are closely tied to a general lack of cybersecurity culture. The solution would require a bespoke cybersecurity education for your organization’s topmost leadership to the least employee.
Having spent millions on highly-complex infrastructure – if you don’t also train your employees, you’ll be a victim of loss.
Because human error will always be the most significant security risk to your organization’s data, phishing emails, an infected USB drive, a malicious download, a scam phone call, etc. are only a few tactics most often used to break in and compromise data. Someone inside always opens the door for these attacks.



